Operational risks and resilience
Table of contents / search
Table of contents
Executive summary
Introduction
Macroeconomic environment and market sentiment
Asset side
Liabilities: funding and liquidity
Capital and risk-weighted assets
Profitability
Operational risks and resilience
Special topic – Artificial intelligence
Retail risk indicators
Policy conclusions and suggested measures
Annex: Sample of banks
List of figures
List of Boxes
Abbreviations and acronyms
Search
General trends
Operational risk in the banking sector has grown in the past years, and operational resilience has become of key relevance. Risks to operational resilience are increasingly systemic as the financial sector has become highly interconnected amid digitalisation. Operational risk capital requirements have increased and account for 10.2% of total requirements (9.7% in June 2023), and they are the second most important component of banks’ risk weights after credit risk. Dispersion across jurisdictions is comparatively low, with only two countries reporting less than 8%, and two countries reporting over 14%.
The scope and significance of operational risk have broadened considerably in recent years, beyond the traditional definition[1]. Exposure to conduct-related operational risk, including, for example, business conduct risk and the risk of financial crime including AML and TF, has remained high as well. Additionally, technological progress and digitalisation significantly influence the scope and importance of operational risk and highlight the necessity to ensure operational resilience. Heightened geopolitical tensions contribute to increased operational risk, in particular related to cyber- and digital risks as well as AML and sanctions compliance risks and require close attention of financial institutions and supervisors. The global IT disruption in July 2024 from a configuration update of US cybersecurity company CrowdStrike also shows the extent of vulnerabilities to operational risks, and the systemic nature of cyber- and ICT risk.
This is not least reflected in RAQ responses, which indicate cyber risks and data security as the highest of the operational risks (79% agreement). Risk of ICT failures as a related risk remains high as well. Conduct and legal risks are identified as the second most significant contributors to operational risk, with a 44% consensus, and a declining trend. Over recent years, these risks have already been primary drivers of operational risk for banks, evidenced by the persistently high levels of legal and redress payments that financial institutions had to render (Figure 66).
Outsourcing risks also continue to increase in banks’ perceptions, according to the RAQ, as reliance on outsourcing business activities and data has grown. Beyond existing risks in this area, operational risks linked to e.g. ICT failures as well as fraud or cyber risks might arise with the introduction of CBDCs.
Source: EBA Risk Assessment Questionnaire
(*) Agreement to up to three options was possible for respondents.
Fraud risk evolved into a major operational risk
Fraud risk has grown significantly in the last 2 years and is considered nearly as relevant as conduct and legal risks, at 42% agreement, according to the RAQ. Risks related to financial crime, but also further digitalisation and technical innovation, including growing usage of AI in financial crime, may have contributed to a continuously growing risk of fraud. This is supported by RAQ responses, which point to payment fraud and fraud by theft or breach of customer credentials, including social engineering, as the main drivers of fraud risk (59% agreement), followed by online and cyber fraudulent activities (52% agreement). On payment fraud, the EBA and ECB in August 2024 released a joint report on payment fraud[2]. The report assesses payment fraud reported by the banking sector across the EU/EEA, which amounted to EUR 4.3 bn in 2022 and EUR 2 bn in the first half of 2023. It examines the number of fraudulent transactions in terms of value and volume, and also presents data based on volumes and also sorted by type of payment instruments, i.e. credit transfers, direct debits, card payments, cash withdrawals, and e-money transactions. The report confirms the beneficial impact of SCA on fraud levels.
Materialised losses from operational risk losses have surged
At approximately 3 million events according to EBA supervisory reporting data, the total number of loss events EU/EEA banks reported in 2023 was at a high level and increased by 3.7% compared to 2022. The number of loss events is at a lower level than in 2021 and 2020, when banks were affected by the impact of the pandemic on their operations. The 2023 number is near its long-term average until 2019. While operational risks have increased since then, a broadly stable number of risk events suggests that banks have stepped up their efforts to manage their operational risk, including in, e.g. enhancing fraud prevention measures and due diligence, reinforcing product approval processes and customer awareness measures (Figure 67).
Source: EBA supervisory reporting data
(*) Gross loss amount from new events and loss adjustments relating to previous reporting periods.
Beyond the number of operational loss events, the impact of losses related to operational risk remains heightened. Total materialised losses from new operational risk loss events reached EUR 17.5 bn in 2023 and increased by approximately 27% compared to the previous year. This amount is near the amount reported at the highs of the pandemic in 2021 (EUR 18.7 bn). The significantly increased volume of new operational risk losses coupled with a high number of loss events suggest a rising impact of operational risk. Materialised losses had a stronger impact and may have been distributed wider across banks than in the previous year. This may be aggravated by high cyber risks, increased fraud risks and continued high conduct risk which may lead to additional materialising losses at a later stage. Accordingly high operational risk losses should remain an issue of concern for the banking sector.
The amount of total losses from new operational risk loss events as a share of CET1 capital also increased to 1.1% in 2023, from 0.9% in 2022. The increase in the ratio was largely driven by higher operational risk loss amounts reported in 2023. But the ratio remains lower than the highs of the pandemic in 2021, and in the long-term average until 2019 (Figure 67).
Since total operational risk amounts only reflect materialised losses from new events, further future losses might arise and could add in the coming year to losses that have already been recognised. These might, for example, relate to IT failures or misconduct payments, as a consequence of court rulings and legal settlements. A possible materialisation of the high fraud risk that banks perceive according to the RAQ might further add to losses.
Operational risk events may not only cause direct financial losses, but might also imply reputational damage, especially as a consequence of events gaining wider public attention, or high impact events. This may result in decreasing revenues in the future if a bank exits certain business areas or faces challenges to retain or attract customers. Costs might, moreover, indirectly increase as a result of materialising operational risk, when higher investments in compliance and governance, or technology, become necessary, or when risk premia for market-based funding increase. Country-by-country data on new operational risk losses in 2023 shows that losses are widely dispersed. While in nine countries operational risk losses were at about 1% of CET1 capital or above, several jurisdictions reported relatively low loss amounts of less than 0.1% of CET1 capital (Figure 68).
Source: EBA supervisory reporting data
Digitalisation and ICT-related risks
Cyber- and ICT-related risk as well as data security continue to be by far the most prominent drivers of operational risk for banks. Risk exposure is also high for consumers, as most of retail banking and corporate banking customers are now primarily using digital channels for their daily banking activities. This reliance on digital and ICT solutions, including outsourcing increased reliance on ICT third-party arrangements, has resulted in increased digital and cyber risk exposure. Risk exposure is also growing amid increased capabilities of cyber offenders, which might expand through the use of AI, cybercrime as a service activities and sophistication of cyber attacks.
Cyber incidents have significantly increased
The ENISA observes a notable escalation in cyber threats and attacks in the latter part of 2023 and the first half of 2024 during a time of rising geopolitical tensions. Cyber incidents have set new benchmarks in both the variety and number, as well as their consequences. ENISA considers ongoing regional conflicts globally as a significant factor shaping the cybersecurity landscape. For the banking sector, they observe a surge in mobile banking trojans in 2024, with a concomitant increase in the complexity of their attack vectors, or ways for attackers to conduct attacks. They also identify the banking sector among most targeted sectors for DDoS attacks, with 12% of all DDoS events across public and private sectors reported in the banking sector[3].
The global FS-ISAC identifies key cybersecurity trends for the financial services sector in 2024. These include generative AI, which enables automating and scaling attacks with few skills required and the financial supply chain as a target, where attackers are, e.g. exploiting cloud systems to compromise software, steal customer data, or hold data for a ransom. Geopolitical events provide the phenomena of ‘hacktivists’, often ideologically motivated opportunities for disruption, as has been evident since the outbreak of the Russian aggression and heightened tensions in the Middle East. Hacktivism has expanded steadily, with major events taking place (e.g. national elections) providing motivation for increased hacktivist activity. New attacker tactics, techniques and procedures include new applications of old crimes, such as QR code phishing and search engine optimisation (SEO) attacks that deliver malware or ransomware, as well as social engineering attacks[4].
Regulators have responded to cyber risks with a range of initiatives, such as the DORA effective from January 2025, which creates a regulatory framework to enhance digital operational resilience.
|
Vulnerability to cyberattacks is high
Confirming observations of an increasing number of cyber incidents on financial institutions since 2023, more than half of banks noted that they had been the victim of at least one cyberattack in the first half of 2024 in their RAQ responses. The share of banks having been the victim of up to ten cyberattacks increased since 2023, to 47% now, while the share of banks falling victim to more than 10 cyberattacks remained stable since 2023 (Figure 69).
Source: EBA Risk Assessment Questionnaire
(*) This relates to an ICT-related incident with a potentially high adverse impact on the network and information systems that support critical functions of the financial entity (Article 3(8) DORA).
RAQ responses also suggest that, while the volume and frequency of cyberattacks as such are unabatedly high, a growing share of responding banks (24% compared to 19% one year ago) report that they faced at least one successful attack which resulted in an actual major ICT-related incident. 1% of banks faced a high number of at least 6 successful attacks. The share of banks which did not experience a successful attack also decreased from 81% a year ago to 75%. These figures indicate that the scope, sophistication and impact of successful cyberattacks across the banking system have increased further. But investments in ICT security infrastructure may bear some fruit, as the number of successful attacks resulting in a major ICT-related incident has not risen further in autumn 2024 compared to spring 2024 in spite of increasing sophistication and a continued high number of attacks. Further investments in ICT and related security are very important, as digitalisation and ICT usage will further expand while vulnerability to cyberattacks will remain high, with expected further sophistication, driven by the growing use of AI.
Operating system outage brings looming ICT risks into focus
On 19 July 2024 a configuration update from US company CrowdStrike, a third-party ICT cybersecurity service provider, resulted in a widespread outage of Microsoft Windows systems. Systems across different sectors, including financial institutions and financial service providers, were disrupted. While most affected financial entities were able to fully restore their systems within the same day, and the CrowdStrike incident did not involve a cyberattack, it represented an event of a major operational disruption and highlights the importance of operational resilience. The incident also pointed to the potentially systemic nature of cyber incidents, which can rapidly spread globally across the financial infrastructure.
European banks of different sizes in many jurisdictions were affected and temporarily experienced IT outages. In retail banking, affected services included, e.g. bank account access, payments, cash withdrawals and other ATM functionalities, and online banking logins. In investment banking, derivative trading volumes saw a notable drop on 19 July, the day of the incident. All affected banks swiftly recovered their services, limiting the overall impact. However, recovery capabilities varied. Institutions should be well-prepared for future potentially more severe incidents, and supervisors need to monitor their readiness. The incident also highlights the importance of testing operational resilience scenarios, better understanding outsourcing and/or concentration risks, considering IT impacts in BCP, having ICT response and recovery frameworks in place, and to establish redundancy measures to ensure continuity of services.
Financial crime risks
The high number of cases of ML/TF involving European banks in recent years has caused substantial reputational damage to the banking system and undermines the integrity of the EU/EEA banking sector. RAQ responses confirm that banks appear to attribute a constant significance to ML/TF risk, with 13% in agreement that it is a main driver of operational risk (13% agreement in spring 2024). Risks related to the implementation of restrictive measures in connection with the Russian war of aggression against Ukraine continue to be a priority for banks. According to the RAQ, risks related to customers’ transactions received from, or sent to, jurisdictions that are subject to international sanctions remain the most relevant financial crime risks for 32% of banks, although with a decreasing trend (34% in spring 2024). Although less significant, the laundering of proceeds of frauds is now considered of high significance risk for 22% banks (18% in spring 2024).
Reporting of AML/CFT weaknesses through EuReCA
From 1 January 2024 to 31 August 2024, 32 national competent authorities reported to EuReCA, the EU’s central database for AML/CFT[5], more than 600 serious deficiencies, or ‘material weaknesses’, that they had detected in a high number of financial institutions exposing them to ML/TF risks. As has been the trend to date, most reports concerned credit institutions, alongside payment, and followed by an increase of deficiencies detected in e-money institutions, compared to the previous report. This reflects the high ML/TF risk EU competent authorities identified within these sectors. Most deficiencies reported in this period were still related to institutions’ approaches to CDD. Most of the measures reported were designed to correct these deficiencies through orders to comply, followed by an increase in orders to implement measures, and fines/administrative pecuniary sanctions (which represents an inverted trend compared to the previous report) (Figure 70). The EBA also started collecting information on natural persons directly associated with ML/TF material weaknesses in May 2024.
Figure 70: Financial crime risks, January 2024 – August 2024
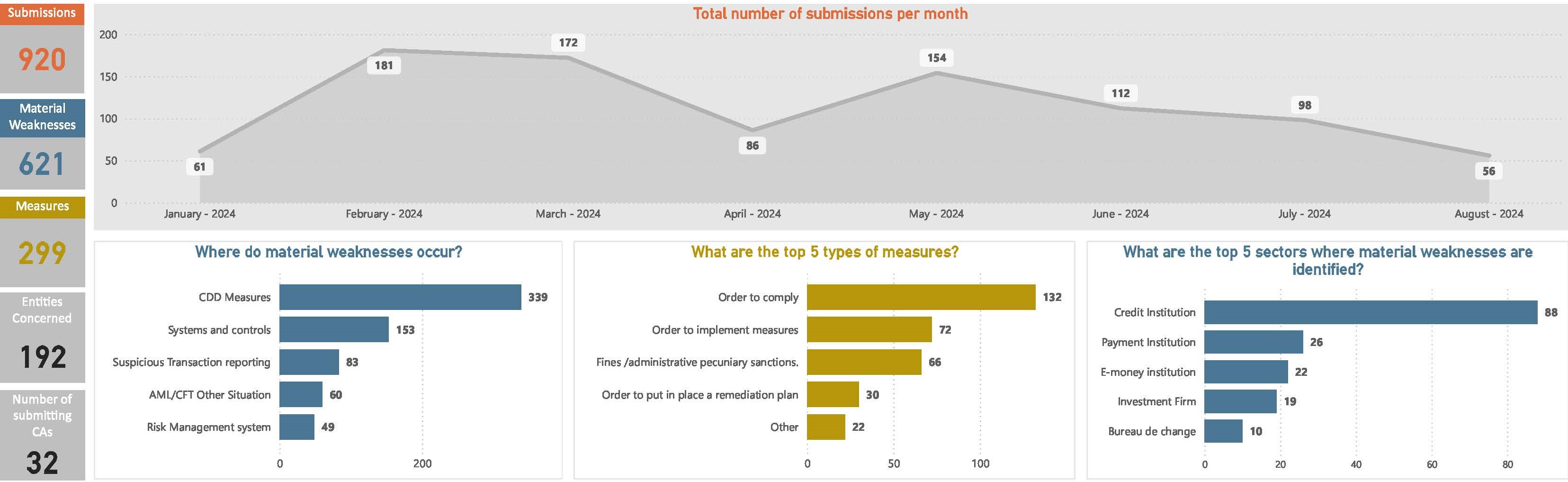
The EBA has continued to address ML/TF-related risks through regulation, including two sets of guidelines on internal policies, procedures and controls to ensure the implementation of EU and national restrictive measures, and guidelines on the ‘travel rule’, i.e. information accompanying transfers of crypto assets and funds.
Further legal and reputational risks
Conduct and legal risk beyond risks related to ML/TF and non-compliance with sanctions is the second most relevant operational risk to RAQ respondents, although it has been steadily decreasing in the last 2 years. About 44% of RAQ respondents consider it the main operational risk, compared to 58% in September 2022. Legal and reputational risks also go beyond those related to digitalisation and ICT-related risks, and include, e.g. unethical business practices, improper treatment of customers and risks related to breaches of sanctions. Concerns about past and potentially continuing unidentified misconduct persist and include, for example, fines associated with financial crime and redress for mis-selling to customers.
New cases of past misconduct causing considerable redress costs and reputational damage continued to emerge in 2024. Misconduct costs come in addition to other operational risks and associated costs banks are facing and can indirectly affect banks’ ability to extend lending to the real economy. Going forward, fines may also affect banks in breach of climate-related targets as agreed with competent authorities. At a systemic level, misconduct can, moreover, undermine trust in the banking system and the proper functioning of the financial system.
Increasing provisions for legal and conduct risk
Data indicates that banks substantially increased their provision for legal and conduct risk in 2023. Net changes in provisions due to pending legal issues and litigation measured as a share of total assets were at approx. 1.9 bps in December 2023 substantially higher than in December 2022 (at approx. 1.3 bps). In the pandemic, these provisions were at a comparable level as reported in December 2023 (at approx. 2 bps in 2021). Considering the relevance of conduct and legal risk as the second most important driver of operational risk, according to the RAQ, higher net changes in provisions due to pending legal issues and litigation appear adequate and may point to expectations of further arising redress costs (Figure 71).
Source: EBA supervisory reporting data
Source: EBA supervisory reporting data
|
Abbreviations and acronyms 
[1] See BIS definition of operational risk in BIS Principles for the Sound Management of Operational Risk.
[3] See ENISA Threat landscape 2024.
[6] Greenwashing is a practice whereby sustainability-related statements, declarations, actions, or communications do not clearly and fairly reflect the underlying sustainability profile of an entity, a financial product, or financial services. This practice may be misleading to consumers, investors, or other market participants.
